Expert Virtualization Security & Hardening

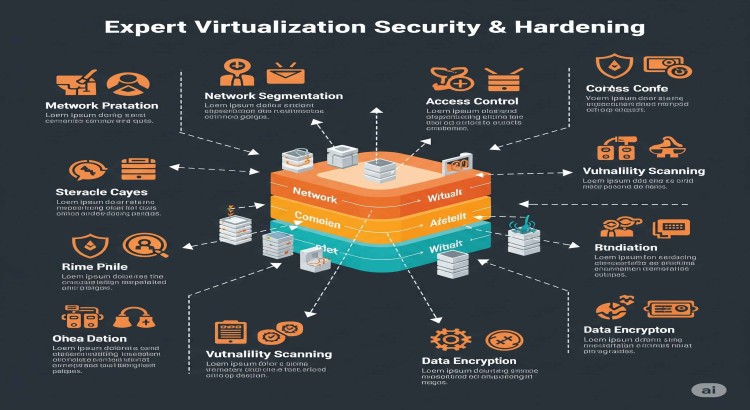
About this Service
Overview:
While virtualization offers significant benefits, it also introduces unique security challenges. A compromised hypervisor or misconfigured virtual machine can expose your entire virtualized infrastructure to severe risks, leading to data breaches, system downtime, and compliance violations. This offer is meticulously designed for organizations seeking to establish an ironclad security posture for their virtualized environments (VMware vSphere, Microsoft Hyper-V, KVM). With 8 years of specialized experience, I provide comprehensive security assessments, hardening services, and policy implementations that protect your hypervisors, virtual machines, and virtual networks from evolving cyber threats. By securing your virtualization layer, you can safeguard critical data, ensure compliance, and maintain the integrity and availability of your virtualized applications, building a truly resilient IT infrastructure.
Tools & Skills:
- Hypervisor Security: VMware ESXi hardening, Hyper-V security best practices, KVM security
- Virtualization Management Security: vCenter Server security, SCVMM security, role-based access control (RBAC)
- Virtual Network Security: Distributed firewalls (VMware NSX), network segmentation (VLANs, VXLAN), virtual network isolation
- Virtual Machine Security: Guest OS hardening, anti-malware for VMs, virtual machine introspection (VMI) awareness
- Identity & Access Management (IAM): Integration with Active Directory/LDAP for centralized authentication
- Logging & Monitoring: Centralized logging (Syslog, SIEM integration), security event monitoring for virtual environments
- Vulnerability Management: Scanning virtual infrastructure for known vulnerabilities
- Patch Management: Strategies for timely patching of hypervisors and guest OS
- Compliance Frameworks: Understanding of PCI DSS, HIPAA, ISO 27001 requirements for virtualization security
- Data Security: Encryption for VMs and virtual disks.
- Automation: Scripting (PowerCLI, PowerShell) for automated security checks and hardening.
How I Work:
My approach to virtualization security and hardening is systematic, proactive, and deeply integrated with your virtual environment:
Virtualization Security Assessment & Risk Analysis:
- Initial Consultation: A detailed discussion to understand your current virtualized infrastructure, critical applications, existing security controls, and specific compliance requirements.
- Hypervisor & VM Audit: Comprehensive assessment of your ESXi hosts, Hyper-V servers, vCenter Server/SCVMM configurations, and individual virtual machine settings.
- Virtual Network & Storage Review: Analysis of your virtual network configurations (vSwitches, port groups) and virtual storage access controls.
- Vulnerability Scan: Utilizing specialized tools to scan your virtual infrastructure for known vulnerabilities and misconfigurations.
- Security Assessment Report: A detailed report outlining identified security gaps, potential risks, compliance deviations, and a prioritized list of recommendations.
Security Architecture Design & Policy Development:
- Secure Virtualization Architecture: Designing a robust security architecture for your virtual environment, including network segmentation, access control, and data protection strategies.
- Hypervisor Hardening Plan: Development of a plan to harden your hypervisors according to industry best practices (e.g., CIS Benchmarks).
- Virtual Machine Security Policies: Defining policies for guest OS hardening, anti-malware deployment, and secure VM configurations.
- IAM & RBAC Design: Designing granular Identity and Access Management (IAM) and Role-Based Access Control (RBAC) policies for your virtualization management platform.
- Logging & Monitoring Strategy: Planning for comprehensive security logging and alerting within the virtual environment.
- Implementation Blueprint: A detailed plan for deploying and configuring security measures.
- Client Review & Approval: Presentation of the proposed design for your review, feedback, and final approval.
Implementation & Configuration:
- Hypervisor Hardening: Applying security configurations to ESXi hosts or Hyper-V servers (e.g., disabling unnecessary services, securing management interfaces).
- vCenter/SCVMM Security: Configuring secure access, RBAC, and auditing for your virtualization management platform.
- Virtual Network Segmentation: Implementing VLANs, private VLANs, or distributed firewalls (e.g., NSX) to isolate virtual machines and control traffic flow.
- Virtual Machine Hardening: Applying security best practices to guest operating systems, including patch management, antivirus deployment, and unnecessary service disablement.
- IAM & Access Control: Configuring user roles and permissions to ensure least privilege access to virtual resources.
- Encryption: Implementing encryption for virtual machines and virtual disks where data sensitivity requires it.
- Logging & Alerting: Setting up comprehensive logging of security events and configuring alerts for suspicious activities.
Testing, Validation & Optimization:
- Security Audits: Conducting internal security audits to verify policy adherence and effectiveness of implemented controls.
- Vulnerability Scanning: Re-scanning the virtual environment to confirm remediation of identified vulnerabilities.
- Access Control Testing: Verifying that RBAC policies are correctly enforced.
- Performance Impact Assessment: Ensuring security measures do not unduly impact virtual machine performance.
- Compliance Verification: Ensuring that implemented controls meet the requirements of relevant compliance frameworks.
Documentation & Ongoing Governance:
- Comprehensive Security Documentation: Provision of detailed documentation including virtualization security architecture, hardening guidelines, IAM policies, and audit logs.
- Best Practices Guide: Recommendations for ongoing virtualization security posture management, regular audits, and patch management.
- Knowledge Transfer & Training: Dedicated sessions to train your IT team on virtualization security best practices, monitoring, and incident response.
Why Choose Me?
- 8 Years of Dedicated Security Expertise in Virtualization: Proven experience in securing complex VMware, Hyper-V, and KVM environments.
- Proactive Risk Mitigation: Identify and address security weaknesses at the virtualization layer before they can be exploited.
- Enhanced Data Protection: Safeguard your sensitive data residing within virtual machines and virtual storage.
- Compliance Adherence: My solutions help you meet stringent regulatory and industry compliance requirements.
- Reduced Attack Surface: Harden your hypervisors and VMs to minimize potential entry points for attackers.
- Peace of Mind: Operate your virtualized infrastructure with confidence, knowing it's secured by an expert.
Service Features
- ● Initial consultation and security assessment of one hypervisor host (ESXi or Hyper-V) and up to 5 associated VMs (up to 5 hours)
- ● Audit of hypervisor configurations and VM settings for security best practices
- ● Identification of critical security misconfigurations
- ● Implementation of essential hardening steps for the hypervisor and up to 5 VMs
- ● Review of existing access controls and recommendations for RBAC
- ● Summary report with identified risks and implemented hardening measures
About the Seller
Reviews (1)

Lucas Pereira
São Paulo, Brazil
Fatima did an outstanding job on our virtualization security project. Her expertise is exceptional, and the quality of her work in hardening our infrastructure was first-rate. We were incredibly impressed with her excellent project delivery—everything was on time and meticulously executed. Furthermore, her post-project support was superb. She is a true professional, and I highly recommend her for any virtualization security needs.
Basic






Join as a freelancer or client
Join as a Freelancer
Join as a Client